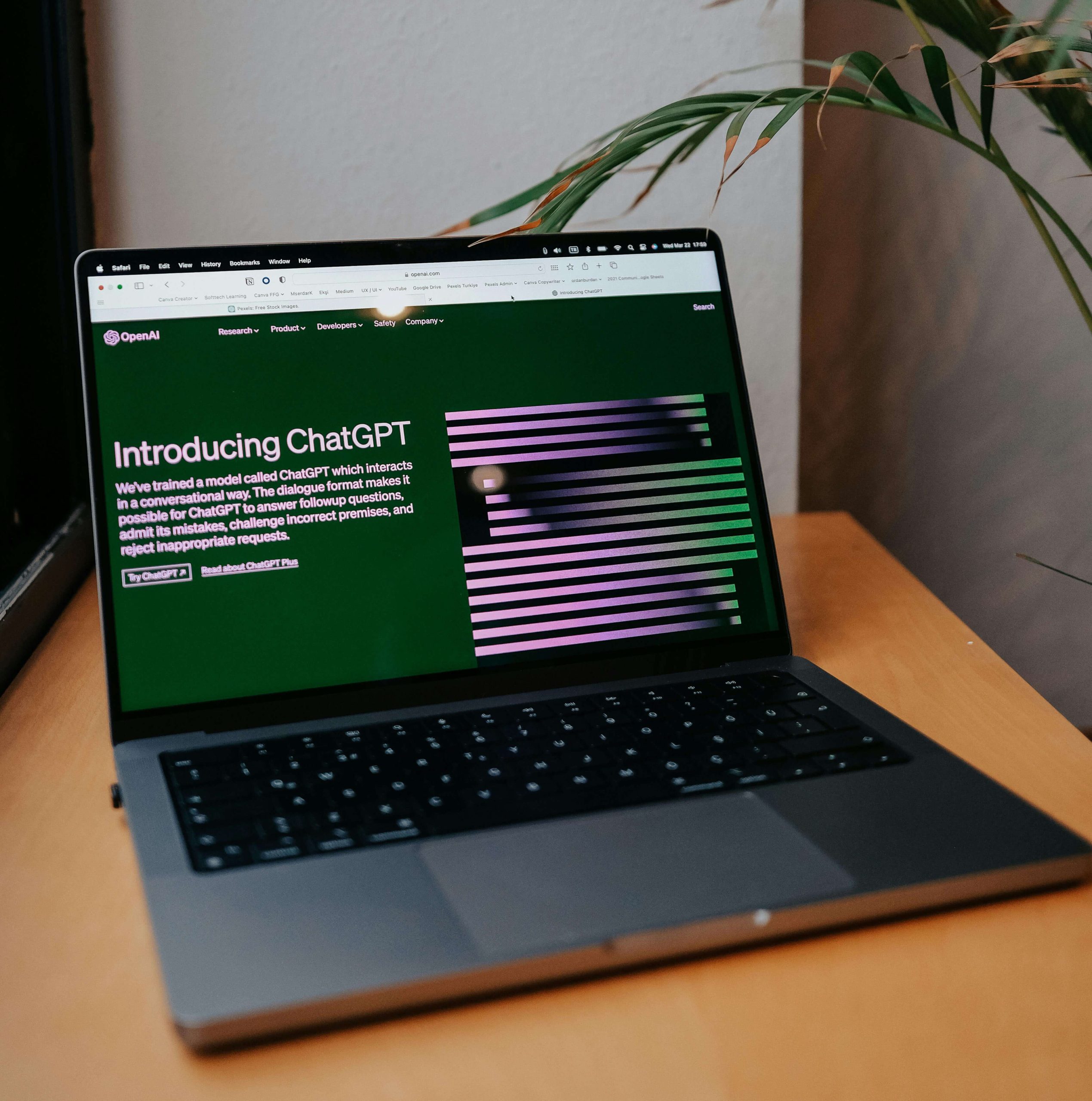
ChatGPT and Why You Should be Cautious
In recent news, the AI-powered chatbot, ChatGPT, made headlines for exposing confidential conversations of its users, raising concerns about privacy and data security. Developed by OpenAI, ChatGPT is renowned for its ability to perform various tasks, from answering questions to generating complex code rapidly. However,...